Another economic downturn will likely happen sooner or later. Inflation, geopolitical and social instability, coupled with supply chain risks, are among the top threats to global economies.
That said, economic slumps are not new. The 2000s dot-com bubble, the 2008 financial crisis, and the global pandemic have proved that businesses can rapidly cope with changing market conditions and successfully reinvent their operations amidst ongoing disruptions.
What’s different now is that information technologies (IT) are now a critical part of corporate crisis response plans and subsequent transformations. IT-resilient businesses recover faster from market disruptions and even see positive impacts of the crises on their business models, operations, and profitability.
But what does IT resilience mean, and how does it correlate with broader corporate objectives? This post (and a free downloadable Playbook!) provides a lowdown.
Setting the Definition Straight: What is IT Resilience?
IT resilience (also referred to as digital or tech resilience) is a set of operational practices that enable organizations to provide sufficient service levels despite disruptions in IT infrastructure availability. In other words, it means ensuring your IT workflows can withstand system failures without experiencing outages, downtimes, or data loss.
IT resilience combines specific functions and defined practices companies implement to strengthen their IT function. Being resilient means more than just using some software or implementing a better chain of command. IT resilience gets stronger, like a muscle, when organizations put effort into these practices throughout their business lifetime. It’s a journey that generates results as long as you stay the course.
In our playbook, we talk about the milestones, challenges, and short-cuts of this journey:
IT Resilience Playbook: A Comprehensive Approach to Strengthening Your IT Processes and Operations
Why Invest in IT Resilience?
Companies benefit from IT resilience not only during extraordinary events but in day-to-day operations, too. New product feature releases, sudden traffic spikes, and other planned or unforeseen events can impact the availability of IT infrastructure.
Planned changes include:
- IT systems cross-integration post-M&A
- Major OS version upgrades or patch installations
- New product or feature releases
- Replatforming from one core platform to another
Unplanned disruptions include:
- Cyberattacks and vulnerability exploit
- Physical environment incidents (e.g., in data centers or server facilities)
- Traffic spikes on the network
- Change in regulatory requirements
IT resilience is crucial to business resilience as companies shift to online channels and accelerate digital transformation. Before that, leaders had viewed IT resilience as an optional investment. CEOs and boards only payed attention when infrastructure disruptions and operational downtimes affected customer satisfaction, growth opportunities, and especially financial performance. And downtime was costly and is getting even more expensive. Over 60% of outages cost organizations more than $100,000 in 2022, up significantly from 39% in 2019.
What’s more, prolonged outages undermine customer trust and can even disrupt the critical infrastructure of entire countries, as these examples show:
- Kakao’s 2022 Outage: A fire incident at Kakao’s data center caused critical service disruptions for 53 million users worldwide, resulting in an 8-hour outage. Without a comprehensive backup system and failover plans, Kakao could not swiftly recover its services and users’ data. Following the incident, the government of South Korea declared its intention to reduce residents’ high dependency on Kakao’s services.
- Rogers 2022 Outage: Rogers, a major Canadian telecommunications company, suffered an outage that lasted 19 hours, impacting 10 million users. The outage was so severe that Canadians could not call 911, withdraw money from ATMs, or pay with cards on public transport. The official reason for the outage is redundancy issues in Roger’s infrastructure that allowed a system failure to enter the update routine.
On the contrary, companies that invest in tech resilience initiatives prevent critical service disruptions and gain other competitive benefits.
Benefits of High IT Resilience
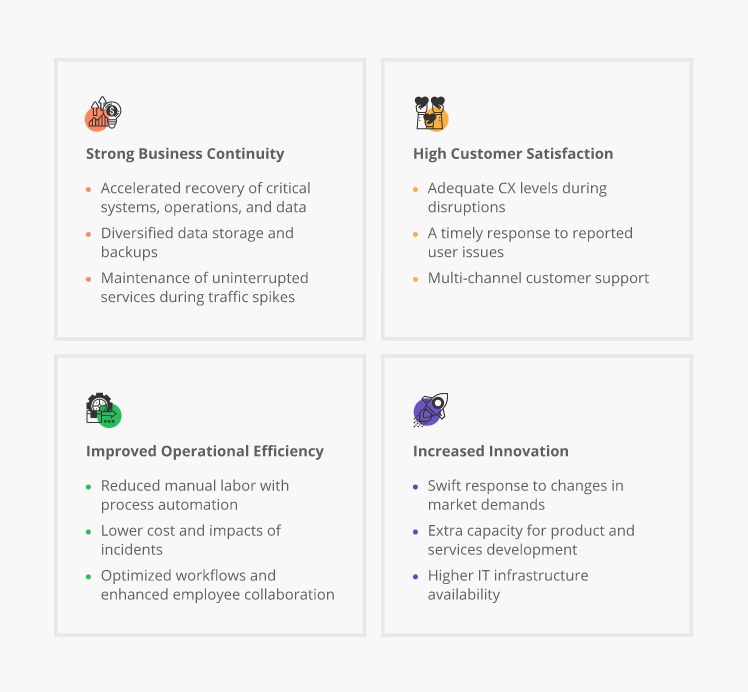
The status of IT resilience transitions from a “good to have” practice to a high-priority investment. As of January 2023, nearly 65% of McKinsey respondents place resilience at the center of their organizations’ strategic progress. They also identify technology as one of the most vital resilience aspects.
Essential Elements of IT Resilience
Tech resilience assumes structural changes across the board, including investments in new functions, workflows, and supporting software components. The central IT resilience components include:
- High service availability
- Strong data protection
- Multi-cloud strategy
- IT infrastructure monitoring
- IT operations knowledge management
High Service Availability
According to Cisco, high availability means that an IT system, component, or application can operate at a high level, continuously, without intervention, for a given period.
Resilient organizations configure and maintain IT systems so they work with minimal (or even zero) downtime, even in the face of high traffic loads and significant infrastructure failures. Essentially, such systems can continuously keep users connected and with access to the same data before the planned or unplanned outage happens.
The basic principles of high availability are:
- Elimination of single point(s) of failure
- Redundancy components in a system
- Regular IT system health checks
- Automated failover and switchover processes
Businesses invest in Site Reliability Engineering (SRE) to achieve high availability. SRE is a set of processes and technologies to achieve greater predictability, scalability, and reliability of software systems.
Strong Data Protection
Data protection involves safeguarding digital information from breaches, thefts, losses, or unauthorized changes. The process encompasses not just physical and digital security of your workloads but also organizational policies and procedures.
Data-destructive events may occur due to tech issues:
- Physical damage to on-premise servers (fire, flooding, etc.)
- Vulnerabilities in third-party software
- Cloud misconfiguration
- Error in IT system
But there’s also the role of circumstantial factors:
- Targeted cyberattack
- Employee negligence
- Shadow IT adoption
- Privilege abuse
- Loss of a device
- Business email compromise
- Stolen identification and keys
Without data protection practices like continuous system health checks, adequate risk management strategy, and regular employee security training, businesses risk damaging customer trust and losing money. According to IBM, the global average total data breach cost is $4.35 million.
Multicloud Strategy
Per Gartner, a multi-cloud strategy is the deliberate use of cloud services from multiple public cloud providers for the same general class of IT solutions or workloads. Going multi-cloud allows companies to cherry-pick the environments that most closely match their workload requirement and budget restrictions.
Advantages of adopting multiple cloud providers:
- Access to best-in-breed features
- Vendor lock-in prevention
- No dependency on on-premise capabilities
- Compliance with different government regulations
- High infrastructure availability
- Improved data governance
Cloud migration, however, can magnify certain operational risks, including potential downtime, data loss, and service interruption. To avoid these, you can partner with a competent vendor, like Edvantis, who can help you create cloud migration plans, design a multi-cloud strategy, and select the right tools and methods to set the migration in motion.
IT Infrastructure Monitoring
Proactive IT infrastructure monitoring ensures timely detection and resolution of possible incidents, preventing potential outages, security breaches, and system downtime.
Other goals of IT infrastructure monitoring are root cause analysis, vulnerability detection and management, infrastructure cost optimization, and legacy systems modernization.
Resilient companies allocate budgets toward tech support and SRE functions to optimize their IT systems.
- Tech support specialists receive constant customer feedback, identify issues of different complexity, and escalate critical requests to SREs and developers.
- SRE specialists ensure timely issue resolution. Moreover, they conduct in-depth infrastructure assessments to seek optimization opportunities, improve system monitoring capabilities, and automate standard deployment processes.
IT Operations Knowledge Management
Knowledge management is a set of practices for gathering, organizing, storing, and spreading information within a company. When your teams proactively write system instructions and share their experience in knowledge bases, it leads to the following benefits:
- System explainability
- Improved system maintenance
- Better issue traceability
- Risk management during staff turnover
- Improved specialist onboarding
- Better tech support workflows
How to Achieve IT Resilience?
“IT resilience isn’t a one-off activity. Rather, it’s a journey and mindset companies need to adopt to achieve technical excellence and recognize weak areas before they cause systemic disruptions.”
Taras Romanyk, Technical Director at Edvantis
At Edvantis, we propose an agile five-step framework for improving IT resilience:
- Define your current IT processes: Identify the gaps in your processes and technology capabilities. Determine if any processes have inefficiencies and vulnerabilities created by legacy components.
- Create a risk management strategy: After evaluating risks associated with your critical IT systems, define a response plan and detail the proposed mitigation strategies. Prioritize each risk based on severity and criticality.
- Analyze customer feedback: Capture what processes, product components, and services need improvements. For that, listen to your customers’ concerns. Build tech support functions to capture, evaluate, and act upon major customer issues or escalate complex issues to SRE and developers.
- Ensure your system availability: Allocate the budget towards SRE and DevOps functions to bring greater predictability, scalability, and reliability to your software systems. Begin formalizing this process by following Google’s SRE maturity criteria and DevOps best practices. If you face a talent gap in this domain, seek external expertise (e.g., via outsourcing).
- Apply insights from IT operations data: Use IT operations analytics (ITOA) tools to leverage data generated by your IT systems. Data analysis helps identify the root causes of critical issues, predict downtimes, and prevent service disruptions.
Building IT resilience starts with gaining awareness of the state of your current IT infrastructure. Then you bridge the gaps by implementing or improving IT operations functions (like tech support, SRE, and DevOps). We discuss all of these strategies in greater depth in our newest playbook.
About Edvantis IT Resilience Playbook
Edvantis’ IT Resilience Playbook assists businesses in improving their IT processes and operations amidst global risks and disruptions. Our guide explores the concept of tech resilience from different angles with data-backed insights on:
- Lessons learned from previous crises: Find out how the business world handled disruptions of the dot-com bubble, the 2008 recession, and the COVID-19 crisis. Explore the success stories of companies that powered through the downturn.
- Impact of tech resilience on businesses: Learn how tech resilience can help you achieve short- and long-term technology excellence and innovation efficiency. With a clear checklist, evaluate how resilient your IT infrastructure is currently.
- Operational best practices: Receive a list of detailed steps and recommendations on how to increase the IT resilience of your organization.
- Tech resilience and outsourcing: Learn how partnering with a mature outsourcing vendor can help you bridge the talent gap and build tech support, SRE, and DevOps practices at an optimal pace and cost.
FAQs about IT Resilience
IT resilience provides benefits beyond extraordinary events by ensuring smooth day-to-day operations. Along with unplanned disruptions such as cyberattacks or regulatory changes, this helps organizations better cope with planned changes such as system integration, upgrades, and releases. Thus, investment in IT resilience is an additional guarantee of customer satisfaction, growth opportunities, and financial performance.
IT resilience and disaster recovery are related but have different scopes and goals. IT resilience focuses on maintaining the availability, continuity, and performance of IT systems and services. On the other hand, disaster recovery deals deals with restoring IT systems and operations to operational status within defined recovery times and target points after a major incident or disaster.
Yes, outsourcing contributes to IT resilience by filling talent shortages, taking over ongoing IT operations consulting tasks, and enabling organizations to build technical support, SRE, and DevOps practices. By partnering with an experienced outsourcing provider, you can leverage their expertise, accelerate the implementation of resiliency strategies, and optimize costs.
Think of the components that play a key role in ensuring the continuity, availability, and integrity of your IT services during disruption. This would be your answer. In general, an effective IT resilience strategy should include servers and data centers, network infrastructure, storage systems, cloud infrastructure, critical applications and software, databases, communication systems, end-user devices, security systems, energy/utilities, and many other components.
There are several ways a cloud strategy can improve your IT resilience. By leveraging cloud services, organizations can offload critical workloads and data to multiple geographically distributed data centers, reducing the risk of single points of failure. Cloud providers also offer built-in backup and disaster recovery capabilities, making it easy for organizations to implement data replication, automated backup, and recovery processes. Additionally, the on-demand nature of the cloud allows organizations to scale resources quickly in the event of traffic peaks or disruptions.
The short answer is yes. By implementing proactive monitoring solutions and employing advanced analytics and machine learning techniques while also conducting regular vulnerability assessments and penetration tests, organizations can monitor and detect potential IT disruptions early, enabling timely containment to minimize business impact.
Measure your IT resilience strategy by conducting regular and extensive testing exercises, simulating various disruption scenarios, evaluating Recovery Time Objectives (RTO), Recovery Point Objectives (RPO), and the accuracy of the recovery process. However, the number and frequency of such testing will depend on the resources, budget, and complexity of your organization’s infrastructure.

