
Companies are increasingly using IT outsourcing services as part of overall capacity management strategy. This has brought up questions regarding the risks of outsourcing, and the benefits and challenges it presents.
Outsourcing in IT is often believed to increase the risks of project failure, but data proves otherwise. According to Delloite’s 2022 Report, 76% of executives reported successfully delegating their IT services to third-party vendors (as part of traditional outsourcing, managed services, or operate services).
Companies entrust third-party vendors with their projects for a variety of reasons:
Source: Delloite’s 2022 Report
Yet, like with any other type of business partnership, certain risks are involved in IT outsourcing. The key to mitigating these risks and maximizing the above-mentioned benefits is an effective outsourcing risk management strategy.
What Is Operational Risk Management?
If you’ve worked on any project at management level, you’ll be familiar with the concept of operational risks.
According to the Basel II regulations, operational risk stands for losses that could originate from suboptimal internal processes, failures in supporting systems, as well as the human factor. Count external events (including regulatory risks) too.
Operational risk management, in turn, is a continual cyclic process that includes risk assessment, risk decision making, and implementation of risk controls. Ultimately, the goal of these actions is to achieve acceptance, mitigation, or avoidance of risk, while also ensuring the resilience of IT systems.
Operational risks happen for an array of reasons, both internal (for instance, lack of stakeholder engagement and external — e.g. the vendor’s weak delivery culture.
In either case, if not managed right from the start, operational risks can result in poor engagement, underperformance, or communication falling short of expectations.
The Common Types of Operational Risk to Account for in IT Outsourcing
Operational risks are some of the key factors contributing to outsourcing failures. Low operational readiness becomes apparent long before your outsourcing project begins. If it isn’t addressed properly, it will impact the entire project lifecycle and strain the partnership with your IT vendor.
Operational risks can be divided into two types: engagement risks and delivery risks.
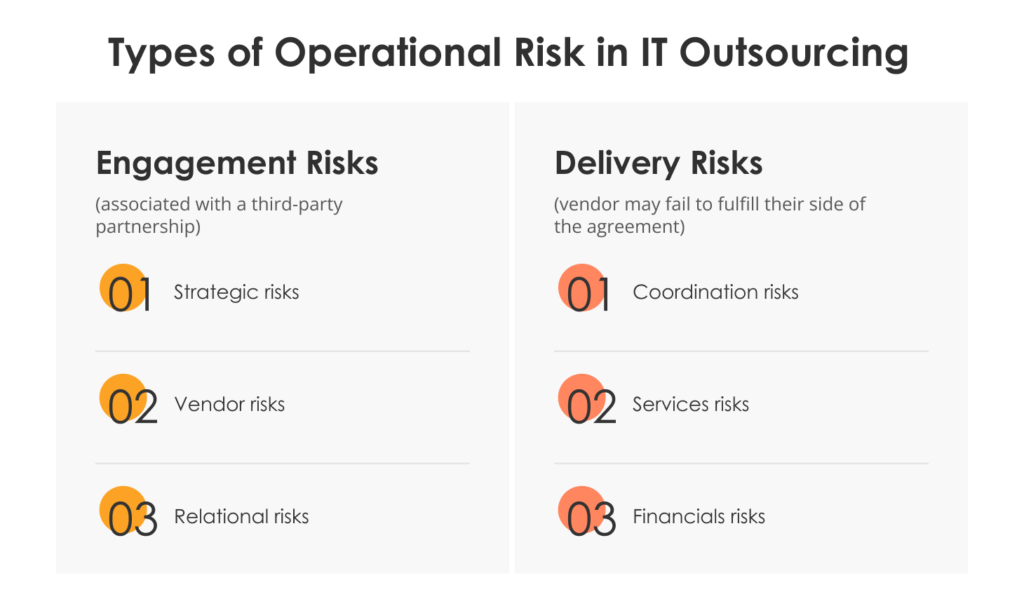
Engagement risks are the overall risks associated with a third-party partnership. These include the following sub-types:
- Strategic risks: the risk that the services or products provided by your vendor will no longer align with your strategic requirements and expectations as your project progresses.
- Vendor risks: the risk that a vendor does not operate as you expected, or provides a service that does not comply with local laws or regulations.
- Relational risk: the possibility that your vendor will fail to maintain an appropriate level of communication, engagement, or management during the project.
Delivery risks encompass the risks that your vendor may fail to fulfill their side of the agreement. For example, by delivering only partial work or services of lower quality. These sub-types can be further grouped as:
- Coordination risks: the risks inherent in having to manage a complex system of relationships, contracts, processes, people, and technologies.
- Service risks: the risks that your vendor’s services or products will fail to meet contractually defined quality standards and expectations.
- Financial risks: the possibility of the project exceeding the set budget due or risks associated with incorrect initial estimates.
Yet, knowing where the common operational risk types may come from is not enough to mitigate them.
Understanding the baseline principles of operational risk management is essential to avoid IT outsourcing mishaps.
Risk Management Strategies: Tips for Effective Outsourcing Risk Management
The key objective of operational risk management lies in identifying, assessing, and monitoring the potential risks that may occur at different stages of your outsourcing project lifecycle. Here are four major activities you should take to ensure a smooth outsourcing engagement.
1. Risk Assessment
Each type of risk outlined in the previous section originates from either processes, systems, people, or external events.
- Processes: all the processes associated with your outsourcing engagement, including but not limited to business processes, administrative processes, support processes, and requirements management processes.
- Systems: all information technology and communication systems, including hardware and software.
- People: all the people involved in your engagement lifecycle, such as Software Engineers, Managers, Designers, and Product Owners.
- External events: market, or regulatory changes, and similar events which cannot be controlled by your organization, can also impact the outsourcing engagement. Note: for the duration of the project, your vendor counts as a potential source of internal (i.e. controllable) risks, not external risk.
Address the combination of these risk types within your operational risk management framework.
2. Outsourcing Readiness Assessment
As briefly mentioned, not all potential causes of project failure lie with the vendor. Your organization may also have gaps in operational readiness for IT outsourcing.
For instance, it might not have proper process capabilities in place to support an external team. Thus, assessing your organization’s readiness for outsourcing is another essential step for managing outsourcing risk. For this you need to:
- Outline your reasons for using outsourcing, and make sure they are justified.
- Ensure you know how outsourcing will fit into your company’s or project’s overall business strategy.
- Create SMART objectives, and set goals and expectations.
- Determine the areas where you expect outsourcing to bring your company the most value.
- Formalize your capacity needs.
- Define, whether there are applications, software, hardware, and devices employees use that IT teams did not authorize (Shadow IT).
By doing all of the above, you ensure that your company’s processes can accommodate the proposed outsourcing service model.
3. Contract and SLA Assessment
Your service-level agreement (SLA) plays a vital role in establishing proper client-vendor relationships. This agreement describes:
- Expected service levels from your vendor.
- Relevant metrics for measuring performance.
- The responsibilities and expectations on each side.
- Actions in case of not achieving an agreed-on level of service
Your selection of SLA metrics should depend on the scope of provided services.As a minimum, they should cover service availability, budget estimates, and technical quality. . As a rule of thumb, simpler metrics are better. Choose IT metrics that can be easily (ideally automatically) collected. Doing so will make monitoring and reporting easier.
The SLA protects both your company and the vendor from misinterpreting any part of a relationship or deliverables. The agreement should ensure that you both have an identical understanding of the project requirements.
Сontract terms play a similar role in formalizing deadlines and obligations, indemnification, handling of confidential information, non-disclosure duration, limits of liability, and termination clauses. Both your contract and SLA should be aligned with the business goals of your engagement.
As part of your operational risk management strategy, you should always have the IT outsourcing services contracts signed:
- Non-disclosure agreement (NDA) ensures the confidentiality of the information you share with your vendor.
- Master Service Agreement (MSA) outlines your future relationship with your outsourcing vendor in terms of key objectives, responsibilities, roles, and services to be provided.
- Statement of Work (SOW) sums up and describes the scope of the project. Countersigning it signifies the beginning of your outsourcing partnership.
4. Strong Practices for Monitoring Delivery
Risk management in outsourcing often focuses heavily on the planning and contract stages. But proper assessment needs to continue throughout your outsourcing project lifecycle.You can achieve this by setting forth relevant performance metrics and KPIs.
There are four major types of KPI are:
- Basic: Apply them to general sources of risk to evaluate whether service requirements are met and deal objectives achieved.
- Reactive. Give you ability to evaluate the effectiveness of your business decisions and determine whether they facilitated the desired outcome.
- Reflective. Use them to monitor high priority risks, and include continuous post-performance monitoring and reporting.
- Proactive. These are placed on high priority risks and include proactive service quality assessments.
The following factors also contribute to successful delivery monitoring:
- A strong software development lifecycle is an essential part of successful strategic product management
- Transparent and regular communication between in-house and vendor teams
- Clear reporting standards, as outlined in your scope of work/contract
- Well-defined change management process.
The combination of all these measures can help ensure consistent management and mitigation of risks throughout the entire outsourcing lifecycle.
5. Business Reviews
Business review is a formal session where you and your outsourcing vendor discuss the completed work, the quality of services delivered, and any risks encountered. Depending on your project, business reviews may occur yearly or quarterly.
Business reviews are an opportunity for you to provide an honest evaluation of your vendor’s progress. For your partner, business reviews are crucial for tailoring their service offerings to your needs and preparing for any extra arrangements (such as team scaling, transitioning to another service model, etc).
As a reference point for future business reviews, you and your vendor can document the input from that meeting in writing.
Regular business reviews with your outsourcing vendor include help:
- Assess the vendor’s performance
- Assure compliance with all contact agreements
- Address recurring cooperation issues
- Identify and manage operational risks
- Outline further collaboration terms
To Conclude
Operational risk management in IT outsourcing is a continuous process. Thus, knowing where your risks lie is key to preventing undesirable outcomes. Back this knowledge by operational risk assessments and risk mitigation based on the collected results. This will help to ensure the sustainability of your outsourcing project lifecycle.
At Edvantis, we help our clients right-size the optimal service model, based on their operational maturity, project type and overall strategic vision. Contact us to learn more about our approach to reducing operational risks during IT outsourcing.







